Global commerce requires trust, and trust can’t exist without transparency. This is particularly true in international payments, but it’s equally important in the way businesses interact. Fortunately there are many excellent business intelligence companies in existence, who can provide a wealth of intelligence to allow you to know your customer, your supplier, or any other counterparty.
But that’s only part of the story.
To be effective, all that wealth of information must be shared, and that’s where existing communication methods begin to let us down.
Let’s explore further, beginning with international payments…
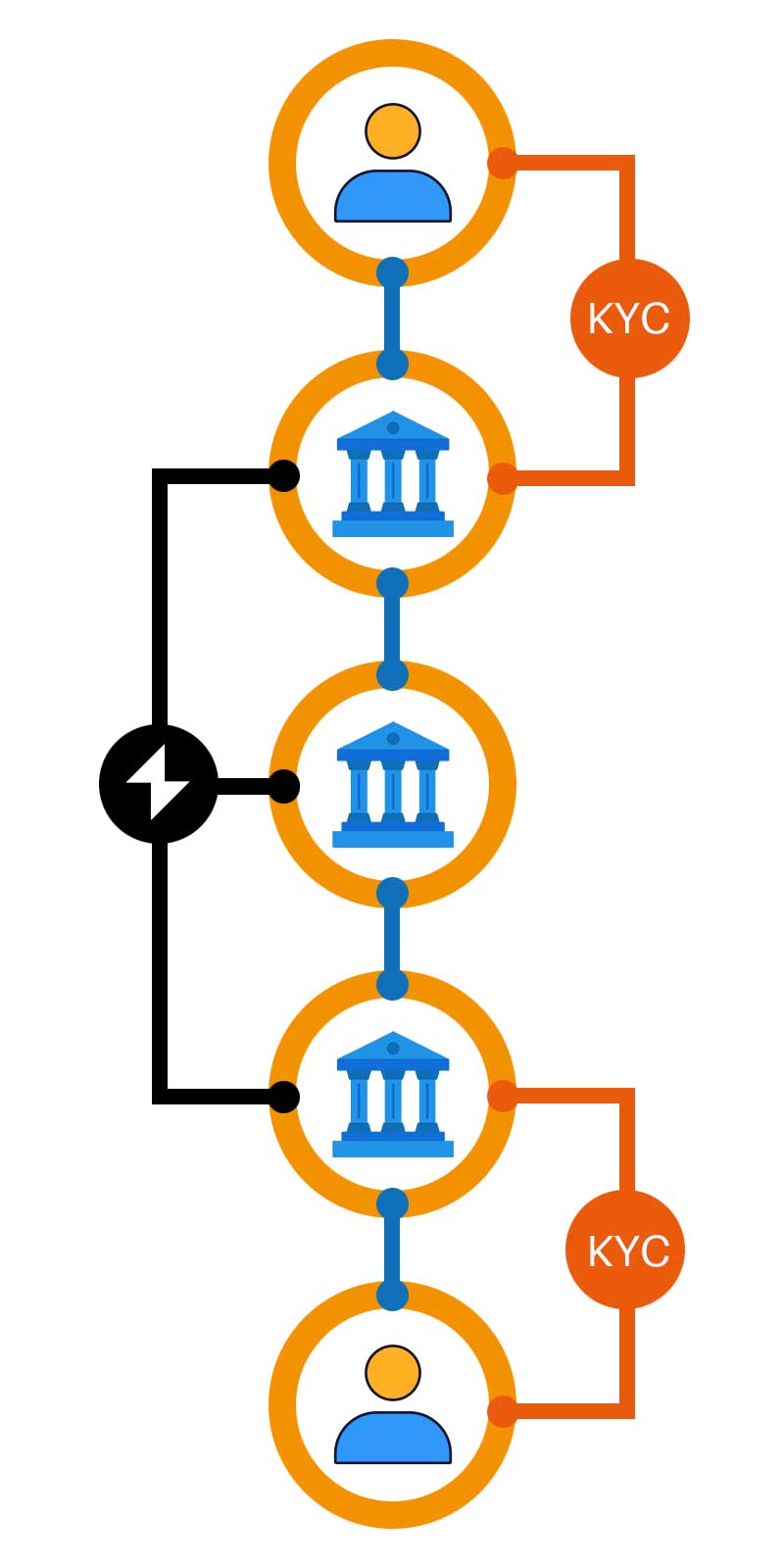
This chart shows a typical cross-border flow. In practice, there’ll often be more intermediaries, but this example gives a fair illustration of what’s going on.
At the top is an importer, who wants to buy from the exporter at the bottom. Each is connected to their own bank (or NBFI), who onboarded them as a customer and has completed the necessary diligence to comply with financial regulations. The importer instructs its bank to make a payment. To accomplish this, there’ll often be intermediate or correspondent organisations. They receive an instruction from the originating bank, usually by SWIFT or Fedwire. They then instruct the receiving bank and the payment can be settled with the exporter.
Except that it can’t.
To fulfil their compliance responsibilities, each of the downstream organisations needs to gather information about the source of funds, and neither SWIFT nor Fedwire has the capacity to convey that information (we’ll discuss how ISO20022 affects this in a moment).
Now, each downstream organisation has to request information from the next party upstream, usually by email. Copy documents can then be sent, by email where size limits allow, or possibly via Dropbox, WeTransfer, Google Docs or various other means. Information becomes fragmented, privacy can be compromised, errors multiply, and there’s no consistent audit trail.
Meanwhile, delays and workload costs multiply. And whn the payment finally gets settled, everyone upstream has to rely on the diligence of the receiving organisation. None of them really knows what has been purchased.


The eKeyiD system is driven by a set of compact codes, each small enough to fit into standard messaging systems such as SWIFT or Fedwire, but with the power to unlock unlimited gigabytes of information. It’s particularly powerful in sharing AML/KYC data between financial organisations, reducing the need for requests for further information, and so speeding and securing more efficient international payments.

It’s widely accepted that only the destination bank holds KYC information on the destination of funds. That’s not necessarily desirable; it’s more of an acceptance of the practicalities of our financial communication methods.
Under the eKeyiD environment, it’s possible, optionally, to require the destination compliance documentation to be added to the information stack, giving true end-to-end transparency

Transparency is desirable, but not at the expense of privacy. In designing the eKeyiD suite, this was constantly at the forefront of our minds. We call it the the PvT - Privacy versus Transparency - balance. We achieve it through our unique data vault, that intelligently identifies types of data and measures access against the identity and privileges of the person or organisation attempting to view the information.
The data vault is based on our patented federated ledger technology, but is able to act as a secure gatekeeper even if you choose to hold data in your own database. Its effect is that eKeyiDs can be shared freely without compromising privacy or confidentiality.
SWIFT’s implementation of ISO20022 is a major step forward in improving transparency, and we fervently support it. From the 140 characters of the existing MT103 payment information, it gives us 199 fields, each of 280 characters. Surely this is enough?
Before we answer that question, it’s worth considering how few organisations have adopted the new standard, despite deadlines for adoption having already passed. And of course, since the US predominantly uses Fedwire, ISO20022 changes nothing there.
But to return to the question: ISO20022 is a text-based system. It has no means of carrying KYC documents, meaning that proofs of identity like passports, business information like incorporation certificates and transaction details like invoices must still be requested and exchanged separately.
The eKeyiD identities provide instant access to all background information, along with an ISO20022 digest of the information as originally entered, ensuring no errors during pass-through of information.
Existing communication methods are fragmented and potentially insecure.
Errors or inaccuracies can multiply as information is collected by one party and then passed to the next. And should an audit or compliance inspection become necessary, there’s no standard mechanism for identifying the information acted upon by each organisation in the chain.
What’s needed is a single source of immutable information that can be retrieved on demand.
...And that’s exactly what the eKeyiD environment delivers. Documents are stored under our patented DotLedger federated ledger system. It’s impossible for any information to be changed - by anyone, including us*. Authorised organisations can view the information at will, and each time they do, that viewing is also added to the audit trail. The result is that everyone works from exactly the same information and can access unlimited data, not just on the onboarding KYC, but of every transaction.
* Not only can we not change the information, we can’t even see it without the express and recorded permission of the data controller. This protects the privacy of your customers and also allows you to control the jurisdiction in which the information is stored.
CertiQi Limited
Emperor's Gate
114a Cromwell Road
London
United Kingdom
SW7 4AG
Copyright ©2026, CertiQi Limited